Brute Force attacks are very common these days, and most websites are vulnerable to such attacks. These attacks have a negative impact on online stores, causing millions or even billions of dollars in financial losses.
In brute force attacks, personal data are misused and violated so this issue makes an alert for store owners.
That is why internet business owners should take this issue seriously and pay attention to it. In this part of the Magento 2 tutorial, we are going to show how to stop Brute Force Attacks in Magento.
If you use Magento, by default the admin and downloader paths can be exploited in a number of ways, and hackers can easily find them and launch a Brute Force attack. In such attacks, random passwords are automatically tested by hackers to enter the admin area until one of these passwords is correct finally.
A brute attack is one of the easiest ways to get a website because it requires no special skills or resources other than patience. The Brute force attacks are trial and error purely. During the attack, hackers try different permissions, and a combination of usernames and passwords to log in to an account. what should we do? Just take a few minutes to read the following solutions.
Learn how to stop Brute Force attacks in Magento
- Customize the path or address of the admin panel.
- Secure your Magento account.
- Protect Downloader folder
- Protect the folder that is related to git
- Keep your store up to date.
- Enable HTTPS for the admin panel.
Solution 1 Brute Force: Customize the admin path
The default backend address for Magento 1 is your-domain.com/admin. This address is available to the public that’s why hackers can exploit it easily, but you can easily change the address to prevent hacker attacks.
Customize your Magento admin panel access path as follows:
First, open the local.XML file from (/app/etc/local.XML) and then follow these tags in order in this file.
(admin -> routers -> admin hml -> args -> frontName)
Now you can see the <! [CDATA [admin]]> and you can change it to your new admin URL.
Now you can flush your Magento store cache from the path (System -> Cache Management -> Flush Magento Cache) to apply the changes.
Solution 2: Secure your Magento account to prevent Brute Force attacks in Magento
2. 1. Do not use the word Admin in your admin panel address.
Most people use the word admin in the admin panel address of Magento Store, we recommend you don’t use it because it is counted as a security issue and hackers can easily guess. It’s better to use your nickname or email address instead of the word admin.
2.2. Use strong passwords.
The best way to protect your Magento store from a vicious attack is to use a strong password and recommend it to other executives.
A strong password has the following features:
- It has more than 8 characters
- Includes number
- Includes characters (using both lowercase and uppercase letters is highly recommended)
- Includes symbols: optional
Solution 3 to prevent Brute Force: Protect the downloader folder
Magento 1 uses the downloader as a folder to install extensions downloaded from the Magento Marketplace, which makes it easy for hackers to attack your Magento website. You can rename it but there is an effective way to protect the downloader folder.
3. 1. Apache
Open the downloader / .htaccess file and add the following code.
order deny, allow
deny from all
allow from x.x.x.x
x.x.x.x is your whitelist IP v4 address.
3.2. Nginx
Open your configuration file of Magento website: /etc/nginx/conf/mywebsite.conf and add the following code.
location / downloader / {
allow x.x.x.x;
deny all;
location ~ \ .PHP $
echo_exec @phpfpm;
}
}
3.3 Protect the local.XML file
The local.XML file contains very sensitive information such as database information, admin panel path, or encryption key. If this information is leaked to the public, you will face serious problems.
To make sure your website is secure, you enter http://your-domain.com/APP /etc/local.XML in your browser; if you can’t access the information, your website is secure else, you can follow the Protect/downloader folder and disable it.
Solution 4: Protect your git file from Brute Force attacks in Magento
Github is popular now, every store uses Github as a control version of its store. The Git folder contains very important information such as repo URL and code files.
You can disable it, from the path: Protect / Downloader Folder.
Solution 5 to prevent Brute Force: Is your store up to date?
Apply the security Patches, you can apply the patches that Magento has released and secure your Magento store.
If you are on Magento 1, consider migrating to Magento 2. Updating extensions and themes on your Magento website will keep your store healthy.
Related posts: Increase Sales by Displaying Related Products in Magento
Solution 6 to prevent Brute Force: Enable HTTPS for the admin panel
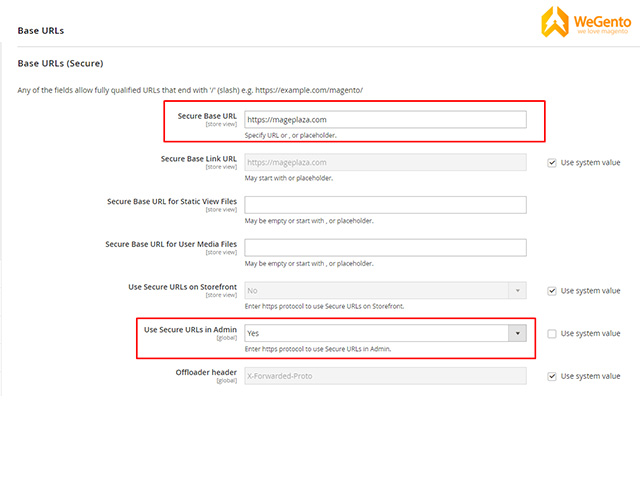
Magento is used for e-commerce transactions and data is often very sensitive, for this reason, it is recommended that all your login details go through a secure connection.
To do this, go to Stores> Configuration> Web.
We hope the solutions provided can help you to prevent Brute Force attacks in Magento.